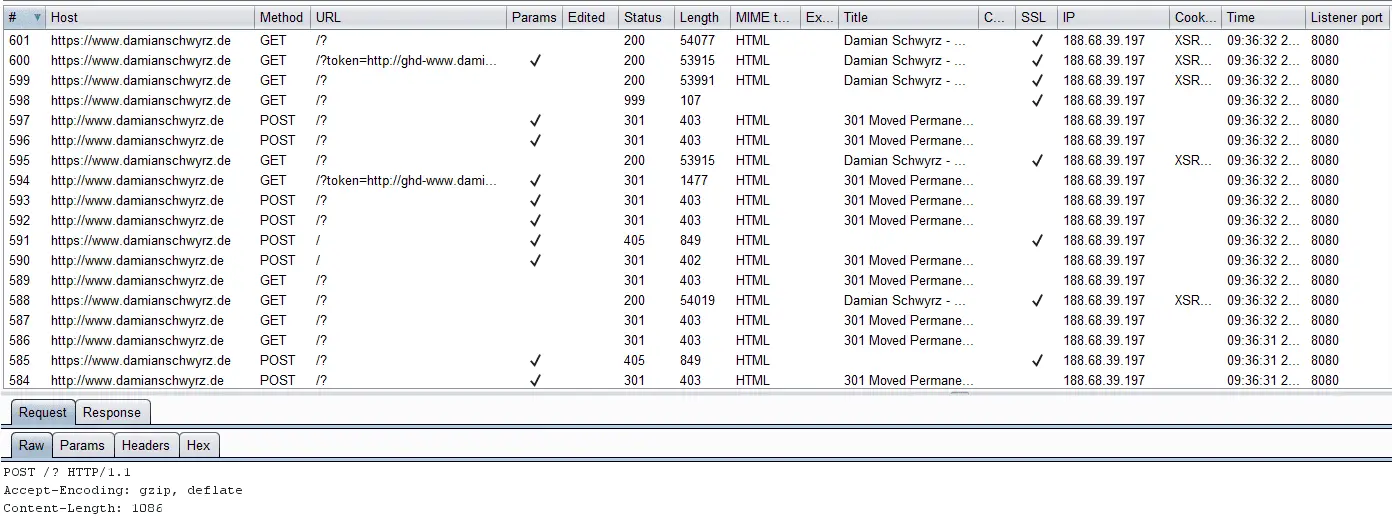
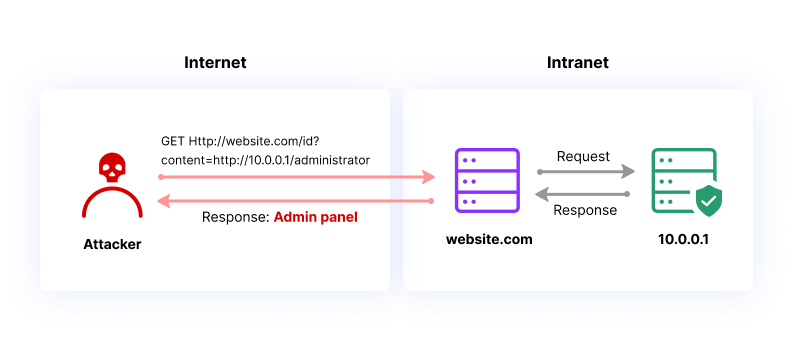
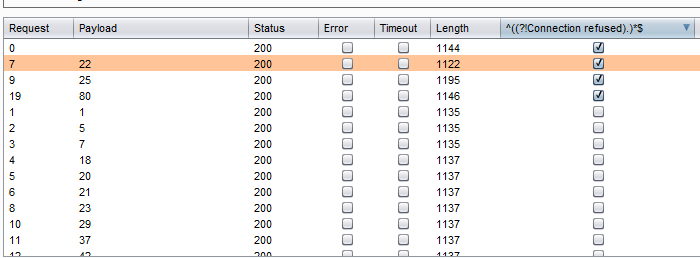
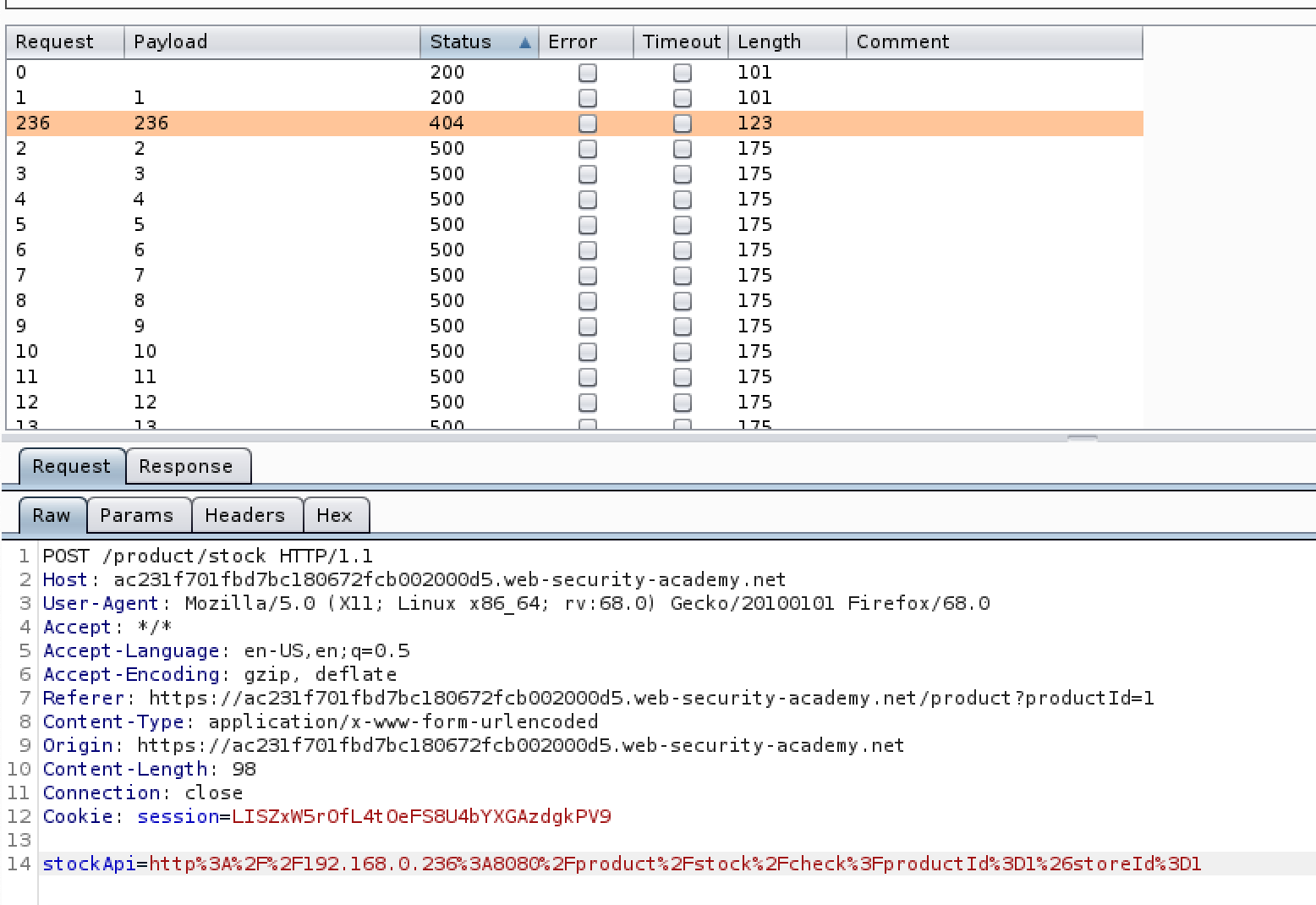
ExploitWareLabs - See-SURF : Python based scanner to find potential SSRF(Server Side Request Forgery) parameters https://github.com/In3tinct/See-SURF | Facebook

MasterSEC on Twitter: "you want to filter URLs with params only from a list but your list is still too big? with this one-liner, you will limit only 5 URLs per endpoint.